Connecting Keycloak to Active Directory¶
Keycloak can federate external user databases. Out of the box support for LDAP (Active Directory) and Kerberos is provided.
To configure the federation proceed als follows:
-
In your Web browser, open the
Keycloak Administration Console: https://localhost:32769 -
Log on with the pre-configured user
adminand passwordSealAdmin1. -
In the
Configuremenu on the left, selectUser Federationto display the entry dialog. -
In the drop-down menu, select
ldap. -
Enter your
ldapconfiguration according to the following table:Name Example Value Comment Edit Mode READ_ONLY Set LDAP backend to read only Vendor Active Directory Selecting the vendor sets up various attributes automatically Username LDAP attribute sAMAccountName The login user. Default is cnRDN LDAP attribute cn For Active Directory it's common to use cnas RDNUUID LDAP attribute objectGUID For Active Directory the UUID should be objectGUIDUser Object Classes person, organizationalPerson, user For Active Directory keep the default value Connection URL LDAP://<fqdn>:389 Connection URL to your AD server, for secure connection use LDAPS://<fqdn>:636Users DN OU=users,DC=example,DC=com Full DN of LDAP tree where your users are Bind DN CN=admin,OU=serviceaccounts,DC=example,DC=com DN of LDAP admin, which will be used to access LDP server Bind Credential Password of LDAP admin configured in Bind DNSearch Scope Subtree Search full tree below Users DN. Default isOne Level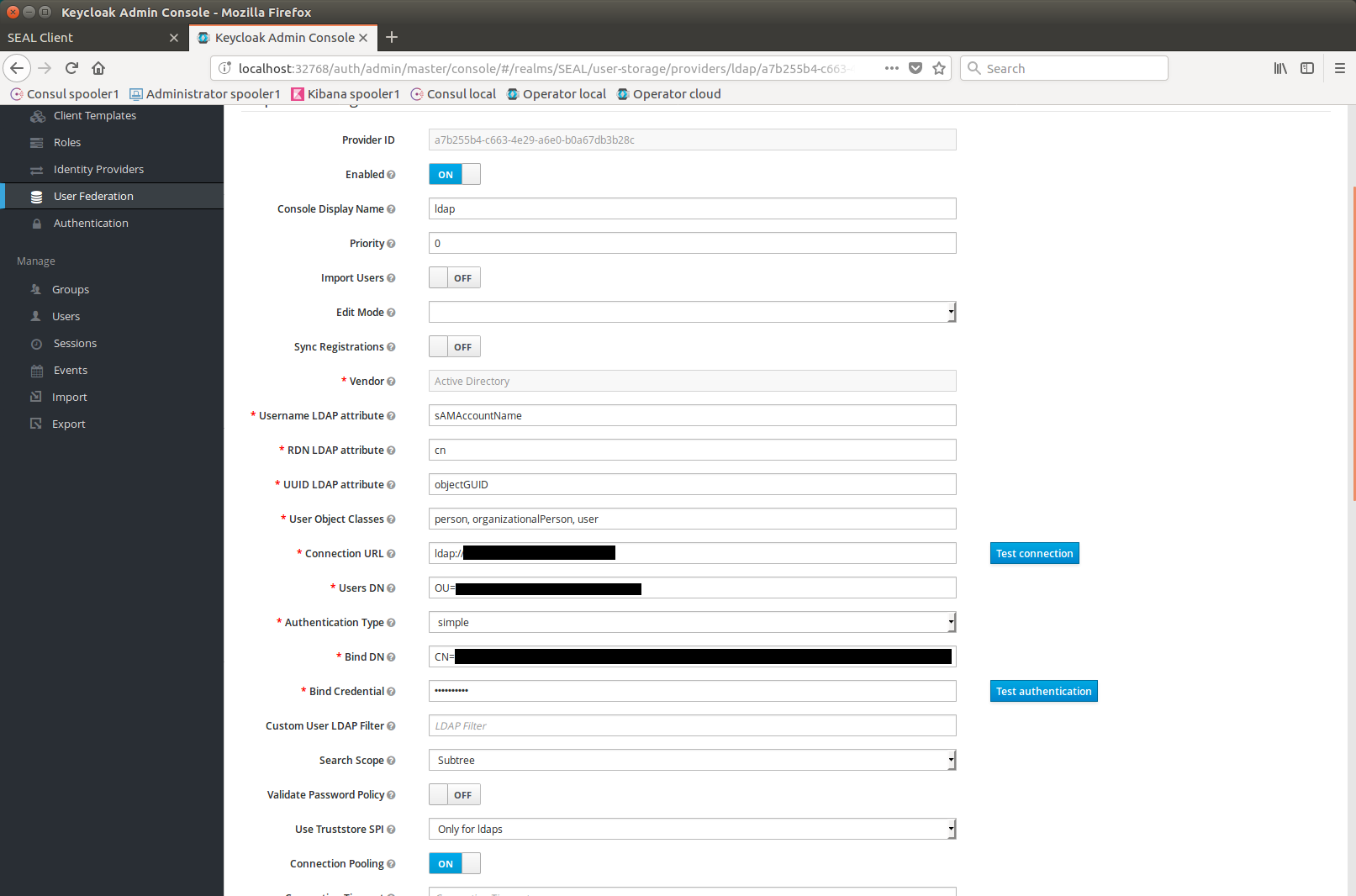
-
Save your settings.
Caution - later changes
When you save the settings of the user federation for the first time, Keycloak adds the mappings for the previously entered LDAP settings in the
Mapperstab. These have to be updated manually, when you change the settings. This is not done automatically.
Hint - log file
LDAP errors will be logged in the "C:\ProgramData\SEAL Systems\log\seal-keycloak.log" file.
Hint - LDAPS
If you use LDAPS, you have to import the following certificates into your Java Key Store:
-
a certificate from the configured LDAP server:
keytool -import -noprompt -trustcacerts -alias <choose-an-alias> -file <root-certificate-file> -keystore <JRE_HOME>\lib\security\cacerts files -storepass changeit -
the
rootcertificate:keytool -import -noprompt -trustcerts -alias <choose-an-alias> -file <root-certificate-file> -keystore <JAVA_HOME>/lib/security/cacerts -storepass changeit