Configuring Predefined Clients¶
Configuring the Redirection URL in the Identity Provider¶
In the identity provider, configure the URLs for redirecting.
-
In your Web browser, open the
Keycloak Administration Console: https://localhost:32769 -
Log on with your user name and password.
If you have not yet changed the default password, see Changing the
adminPassword. -
Open the
Manage realmsmenu on the left.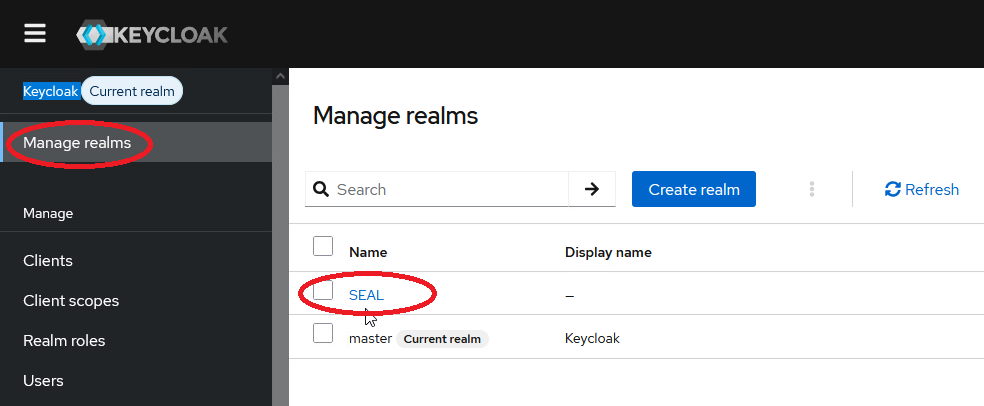
-
In the list, select the
SEALrealm. -
In the
Managemenu on the left, selectClientsto open the client list.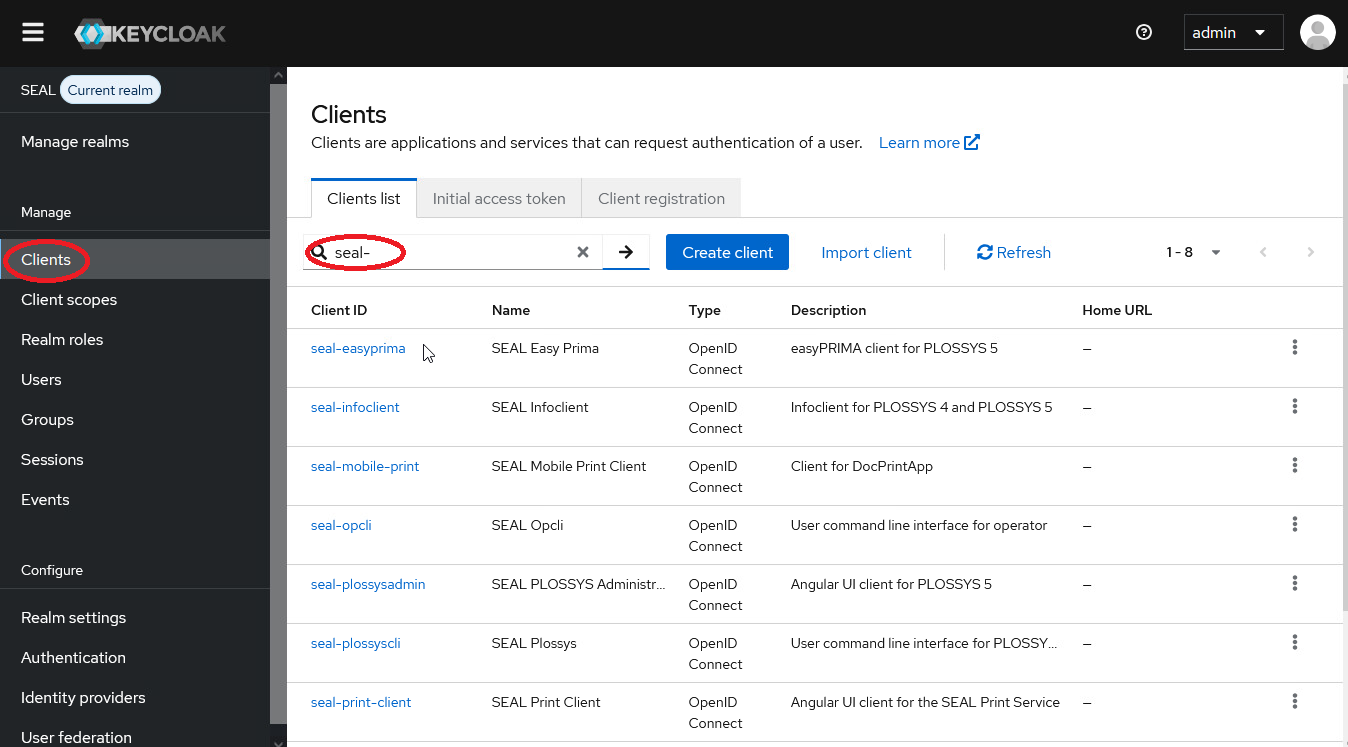
-
In the
Client IDcolumn, select the client you wish to configure.This description uses PLOSSYS Administrator as an example:
seal-plossysadminFor a list of currently available clients, see SEAL Clients.
-
In the
Settingstab, select theAccess settingssection.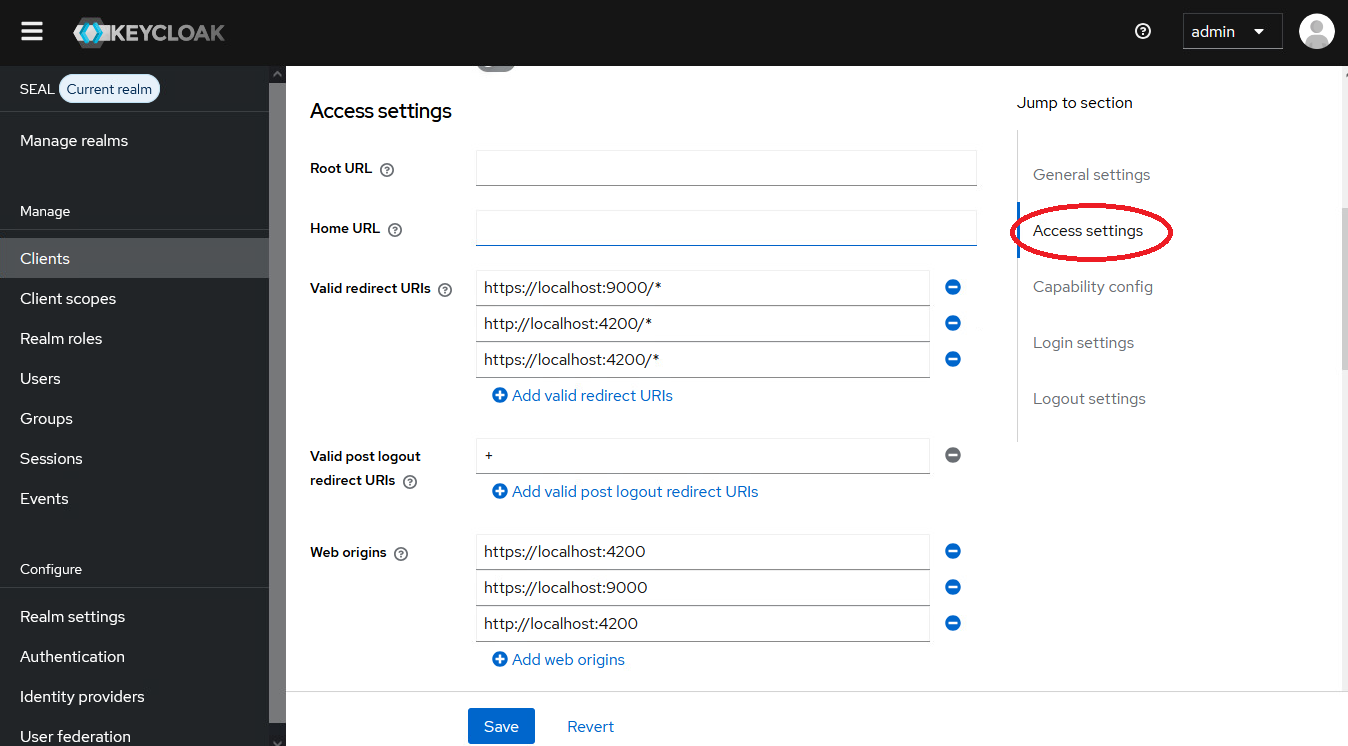
-
In
Valid Redirect URIs, replacelocalhostwith the server name, on which the selected client is installed.with:
-
Valid Redirect URIs:URLs to which the user is redirected after a successful logon.
Example
-
PLOSSYS Administrator redirects to Keycloak to do the authentication.
-
Authentication in Keycloak
-
Keycloak redirects back to PLOSSYS Administrator.
Caution - lower case
The server name in
Valid Redirect URIshas to be specified in lower case. -
-
In
Web Origins, enter the same server name as used inValid Redirect URIs.with:
-
Web Origins:URLs for which Cross-Origin Resource Sharing (CORS) is allowed.
-
-
Save the settings.
-
Repeat the steps 5-10 for any other client you whish to configure.
For a list of currently available clients, see SEAL Clients.
Background Knowledge¶
JSON Web Token¶
The clients receive the user's identity encoded in a secure JSON Web Token (JWT), named ID token. It is issued by the identity server, here Keycloak, and obtained via standard OAuth 2.0 Code Flow supporting Web applications.
Example of a JWT content
{
"name": "hugo",
"preferred_username": "Hugo",
"given_name": "Hugo",
"family_name": "",
"email": "hugo@sealsystems.de",
"iat": 1546860576,
"exp": 1572780576,
"iss": "https://<server_name>:32769/realms/seal-operator",
"sub": "hugos-id"
}
Relationship Between the Settings¶
The issuer property (iss) in the ID token is a unique name created by the identity provider. Its value is an arbitrary string, which is different for each identity provider and has to be determined individually.
If you use Keycloak as identity provider, the value contains the URL by which the service can be accessed through the network. Therefore, the value in the example above will change, if the service is accessed from a different device than localhost.
Caution - identical configurations
For security reasons, the ID_PROVIDER_NAME configuration in the above example has to be identical to the iss entry in the ID token and has to be configured appropriatley.
The AUTH_ISSUER_URL contains a URL pointing to the address by which the identity server can be accessed through the network.
If you use Keycloak as identity provider, the value in AUTH_ISSUER_URL is identical to the one in ID_PROVIDER_NAME.